Preventing modification of /etc/ld.so.preload with SELinux
The /etc/ld.so.preload is an environment variable in Linux that specifies a list of dynamic shared object (DSO) libraries to be preloaded before any others when a program is executed. These libraries can override functions and behaviors of other libraries, allowing for interception and modification of system calls and program behavior. This feature is often exploited by rootkits, malicious software designed to stay hidden with unauthorized access and control over a system.
In terms of Linux user-space rootkits, tracking modification or creation of /etc/ld.so.preload is crucial due to its potential for abuse. User-space Linux rootkits often manipulate this file to load their own malicious libraries, enabling them to hide processes, files (also /etc/ld.so.preload itself!), network activity, and other malicious actions.
Having baseline and monitoring changes to /etc/ld.so.preload helps in detecting, but how to prevent this modification, so even root can't do it easily?
For RHEL-based Linux distros, you can use SELinux. Just create a dedicated SELinux policy module, load it, change the context of the target file and that's it! And don't forget to switch on the secure_mode_policyload - otherwise, modification will be possible as soon as SELinux is put into permissive mode, so watch out!
Here is the step-by-step instruction:
# yum install selinux-policy-devel
# mkdir /root/selinux-no-write
# cd /root/selinux-no-write
# vim nowrite.te
policy_module(nowrite, 1.0)
type etc_nowrite_t;
fs_associate(etc_nowrite_t)
# make -f /usr/share/selinux/devel/Makefile nowrite.pp
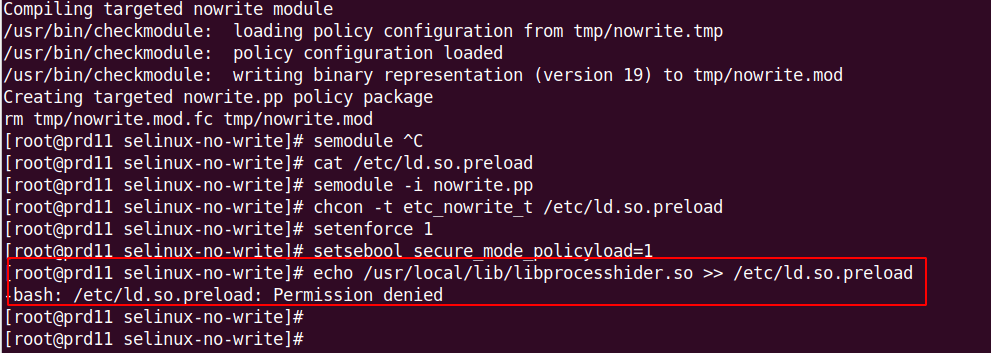
# semodule -i nowrite.pp
# chcon -t etc_nowrite_t /etc/ld.so.preload
# setenforce 1
# setsebool secure_mode_policyload=1
# echo /usr/local/lib/libprocesshider.so >> /etc/ld.so.preload
Want to learn more? Take a look at the full agenda of the self-learning course "Linux Attack and Live Forensics" + 90 days access to PurpleLabs or ping me if you want to organize a private training for your team onsite. Remember, a hands-on approach, focus on goals, thinking out of the box, connecting the dots, and broad view of Linux threats, detection, and forensics - this is the essence of a modern approach for closing the gaps in Linux-oriented cyber security knowledge, and thanks to PurpleLabs Cyber Range and dedicated materials you all have it in one place.
Analyze user space and kernel space rootkits, create low-level Linux attack paths, know better Linux internals, improve your Linux detection, understand the need for Linux telemetry, and stay prepared for Linux threats. The special 30% off promo code after the Hack In The Box Conference in Phuket goes here. The promo code is valid for 14 days (until 13 September), so grab your access now: